EWA Client Application Authentication
This document outlines the transition from our current OpenID Connect (OIDC) authentication flow to a new OIDC compatible security profile. The implementation will enhance our security posture, improve user experience, and simplify client configuration while maintaining compatibility with existing systems.
Current Authentication Flow
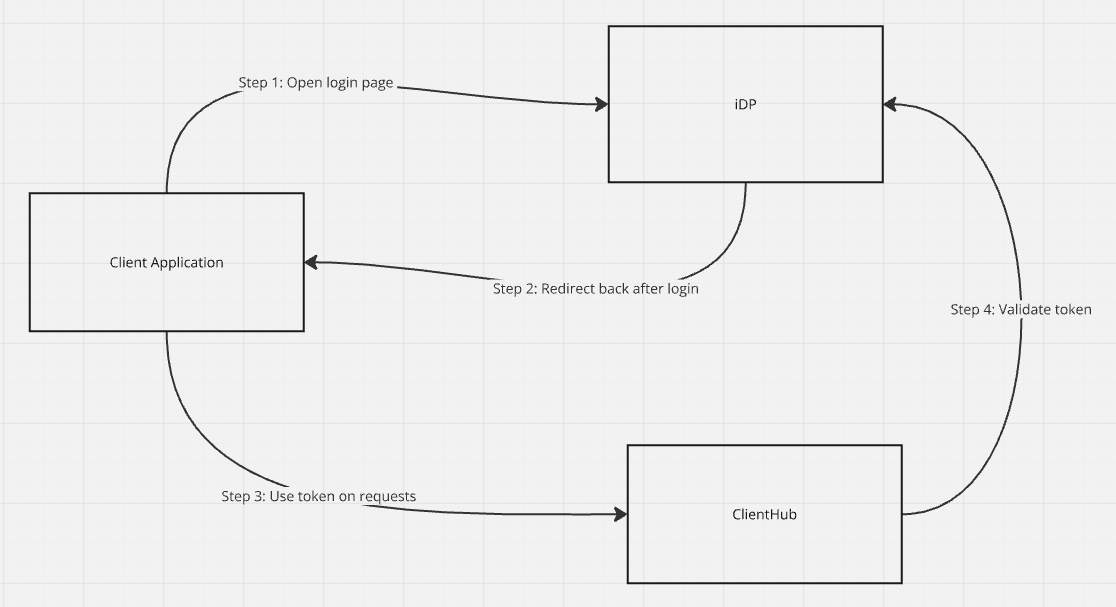
Our existing authentication system operates with direct communication between the Client Application and Identity Provider (IDP), followed by token usage for ClientHub requests:
- Client Application opens login page, connecting directly to IDP
- IDP redirects back to Client Application after successful authentication
- Client Application stores and uses tokens for requests to ClientHub
- ClientHub validates tokens with IDP for each request
OIDC-Compatible Authentication Flow
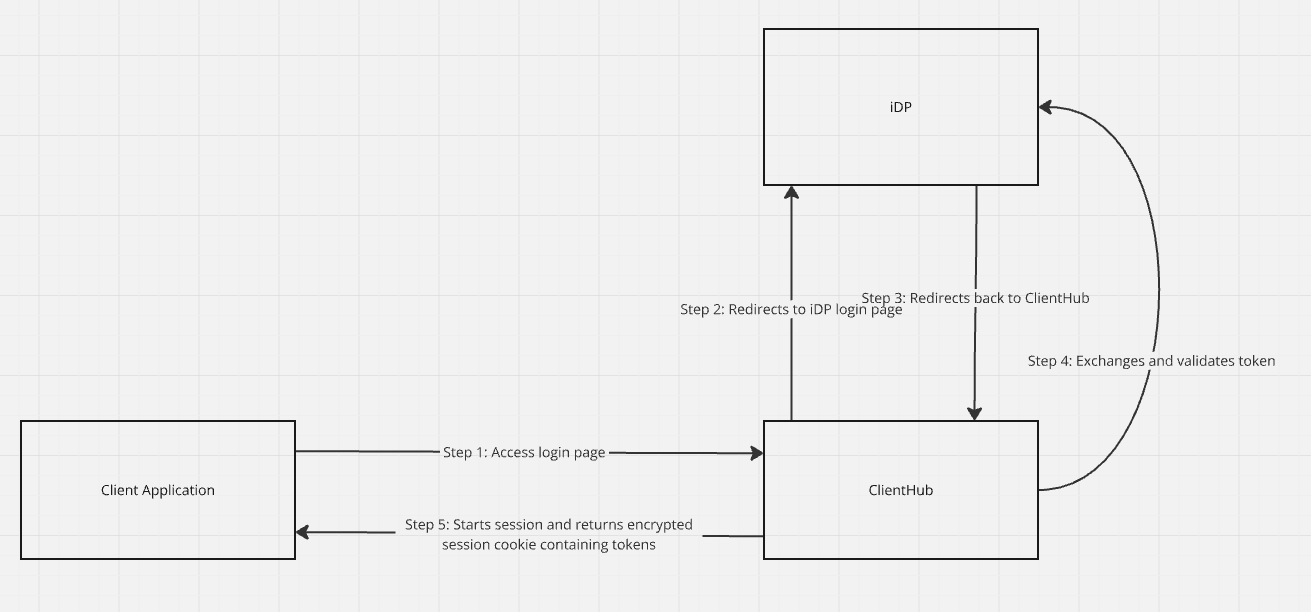
The new implementation centralizes authentication handling through ClientHub, following OIDC security standards:
- Client Application accesses login page on ClientHub
- ClientHub redirects to IDP login page
- IDP redirects back to ClientHub after successful authentication
- ClientHub exchanges and validates tokens with IDP
- ClientHub establishes session and returns encrypted cookie containing tokens to Client Application
Key Improvements
- Centralized Security Model: ClientHub manages token exchange, validation, and session handling
- Reduced Client Complexity: Minimal security configuration required on client side
- Enhanced Session Management: Encrypted session cookies replace per-request token validation
- Unified Authentication Pattern: Consistent implementation across web and native applications
- Standards Compliance: Full alignment with OIDC security profile best practices
Implementation Benefits
Technical Advantages
- Simplified Architecture: Linear communication flow with ClientHub as coordinator
- Reduced Network Overhead: Fewer authentication-related requests after initial login
- Improved Security Posture: Token exposure minimized through encryption and centralization
- Scalable Authentication: Consistent pattern allows easier onboarding of new applications
- Reduced configuration of Client application: Moving the responsibility to ClientHub you can change authentication configuration of Client Application without changing it on the Client. Client only needs the URL to ClientHub.
Business Impact
- Development Efficiency: Reduced client-side security implementation requirements
- Maintenance Simplification: Centralized security updates and improvements
- User Experience Enhancement: More seamless authentication process
- Compliance Readiness: Alignment with current security standards and practices